
In this hands-on Cybersecurity Simulation, participants act as executives and IT leaders facing cyberattacks. They balance prevention, detection, and response while managing financial, reputational, and regulatory risks under real-time pressure.
Cyber risk assessment and threat prioritization
Security investment trade-offs (technology, people, processes)
Incident detection and rapid response
Crisis communication and reputational risk
Regulatory compliance and reporting obligations
Phishing, ransomware, and insider threat scenarios
Business continuity and resilience planning
Collaboration between IT, leadership, and legal functions
Ethics of data privacy and surveillance
Post-incident learning and system improvement

Review cyber threat intelligence and system vulnerabilities
Decide how to allocate budgets to prevention, detection, and training
Respond to simulated cyberattacks with coordinated actions
Communicate incident updates to boards, regulators, and the media
Negotiate trade-offs between operational continuity and data security
Reflect on post-incident lessons and resilience strategies
By the end of the simulation, participants will be able to:
Identify and prioritize cybersecurity risks in business contexts
Balance investment across prevention, detection, and response
Lead coordinated responses to complex cyber incidents
Communicate effectively with stakeholders during crises
Understand regulatory and compliance obligations in cybersecurity
Build resilience into business continuity planning
Manage reputational impacts of cyber breaches
Reflect on ethical dimensions of data security and privacy
Collaborate across technical and leadership roles under pressure
Strengthen decision-making under uncertainty and time constraints
The simulation’s flexible structure ensures that these objectives can be calibrated to match the depth, duration, and focus areas of each program, whether in higher education or corporate learning.
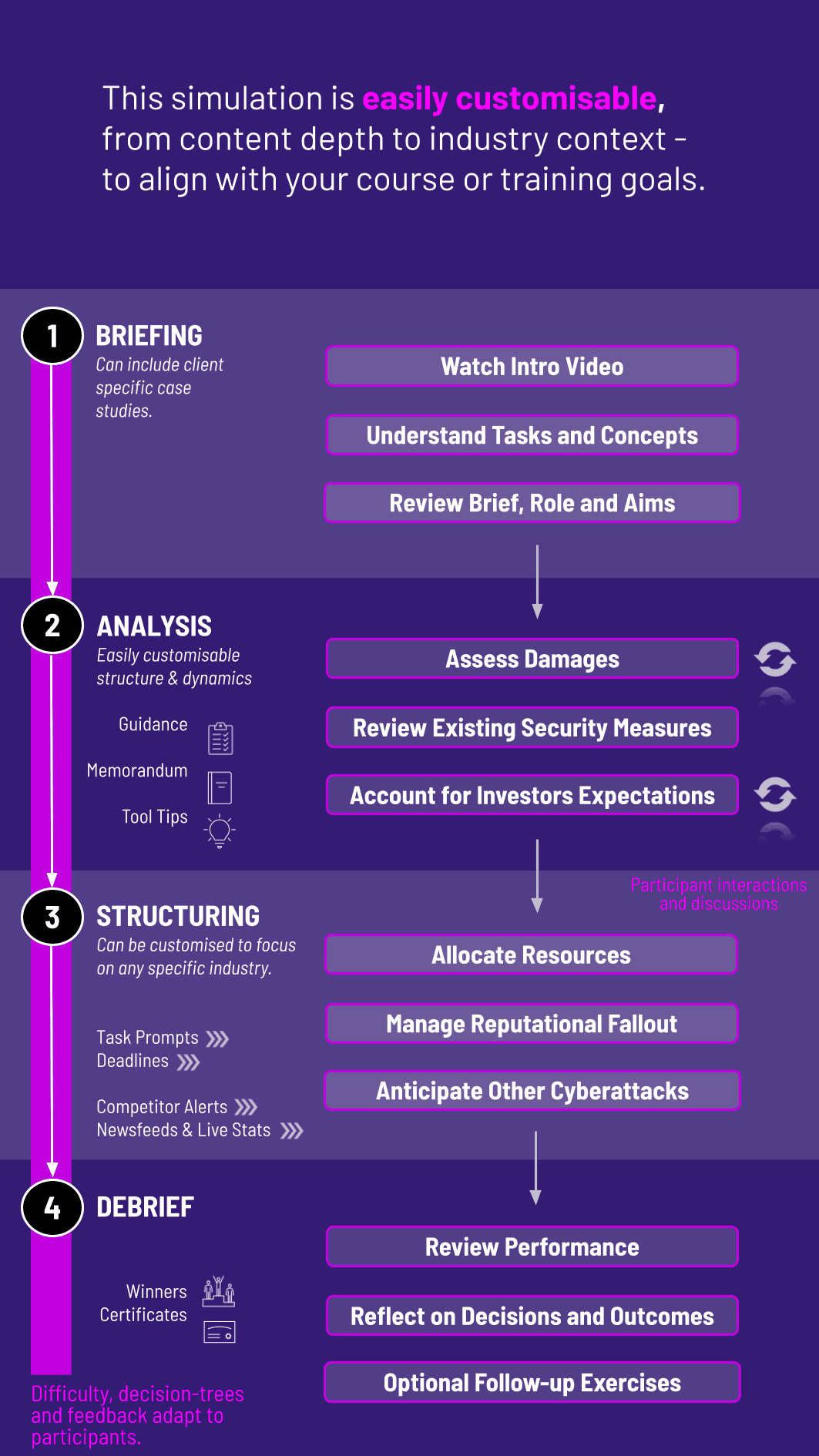
This simulation can run individually or in teams and works in academic and professional training contexts. Each cycle simulates a phase of cyber risk management.
1. Receive a Scenario or Brief: Participants are introduced to a cyber risk context - such as a ransomware attack or insider threat - with objectives and available resources.
2. Analyse the Situation: They review system vulnerabilities, incident data, and stakeholder expectations to prioritize responses.
3. Make Strategic Decisions: Participants decide how to allocate resources, respond to threats, and communicate internally and externally.
4. Collaborate Across Roles: Teams role-play as IT, leadership, legal, or communications leaders to align responses.
5. Communicate Outcomes: Participants craft press releases, board updates, or regulator reports explaining their actions.
6. Review and Reflect: Feedback highlights financial impacts, reputational consequences, and system vulnerabilities. Participants reflect and iterate in subsequent rounds.
Do participants need IT expertise? No. The simulation is accessible to all and focuses on leadership and strategy.
What kinds of attacks are included? Scenarios cover phishing, ransomware, insider breaches, and data loss.
Can it be customized for industries? Yes. It can reflect banking, healthcare, government, or corporate environments.
Is crisis communication part of it? Yes. Participants draft communications for boards, regulators, and media.
Can this run online? Yes. It’s suitable for in-person, online, or hybrid delivery.
How long does it run? It can be delivered in short workshops or multi-day courses.
Is regulatory compliance covered? Yes. Scenarios integrate reporting obligations and legal considerations.
Can teams role-play different functions? Yes. Roles like CIO, CEO, and legal counsel encourage collaboration.
Is this simulation suitable for executives? Absolutely. It’s designed for both technical and non-technical leaders.
How is performance measured? By financial stability, stakeholder trust, compliance, and long-term resilience.
Effectiveness of incident response strategies
Quality of risk prioritization and resource allocation
Clarity and persuasiveness of crisis communication
Responsiveness to new threats and escalation
Collaboration and leadership under pressure
You can also include memo writing and debrief presentations as part of the assessment structure. Additionally, you can also add a built-in peer and self-assessment tool to see how participants rate themselves. This flexibility allows the simulation to be easily integrated by professors as graded courses at universities and by HR at assessment centres at companies.
Join this 20-minute webinar, followed by a Q&A session, to immerse yourself in the simulation.
or
Book a 15-minute Zoom demo with one of our experts to explore how the simulation can benefit you.